Existing customers
Step 1: Allow Airwallex customers to authorize your application
Implement a "Connect to Airwallex" button on your user interface. Users can click this button to connect their Airwallex account to your application. Upon clicking, the button should initiate our OAuth authorization flow URL:
https://airwallex.com/oauth/authorize?response_type=code&client_id=YOUR_APPID&redirect_uri=YOUR_REDIRECT_URI&scope=YOUR_SCOPES

Specify all the scopes within YOUR_SCOPES that you plan to leverage in the authorization flow during integration. This authorization flow is mandatory when users initially connect to your application and is also necessary when your application requires access to additional scopes.
Customers will be directed to log in to their Airwallex account, choose the specific account they wish to link to your application, and review the permissions that your application is seeking.
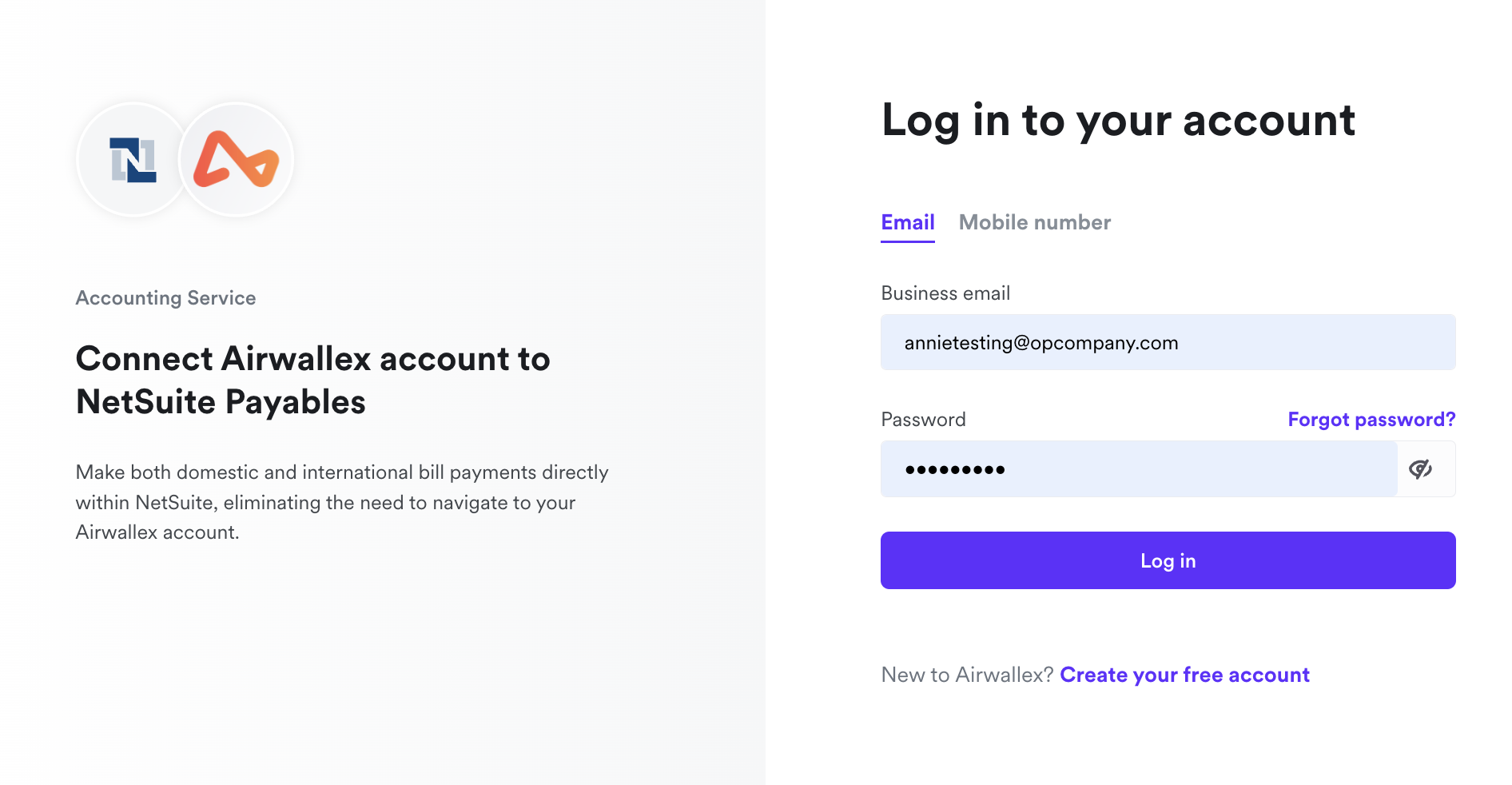
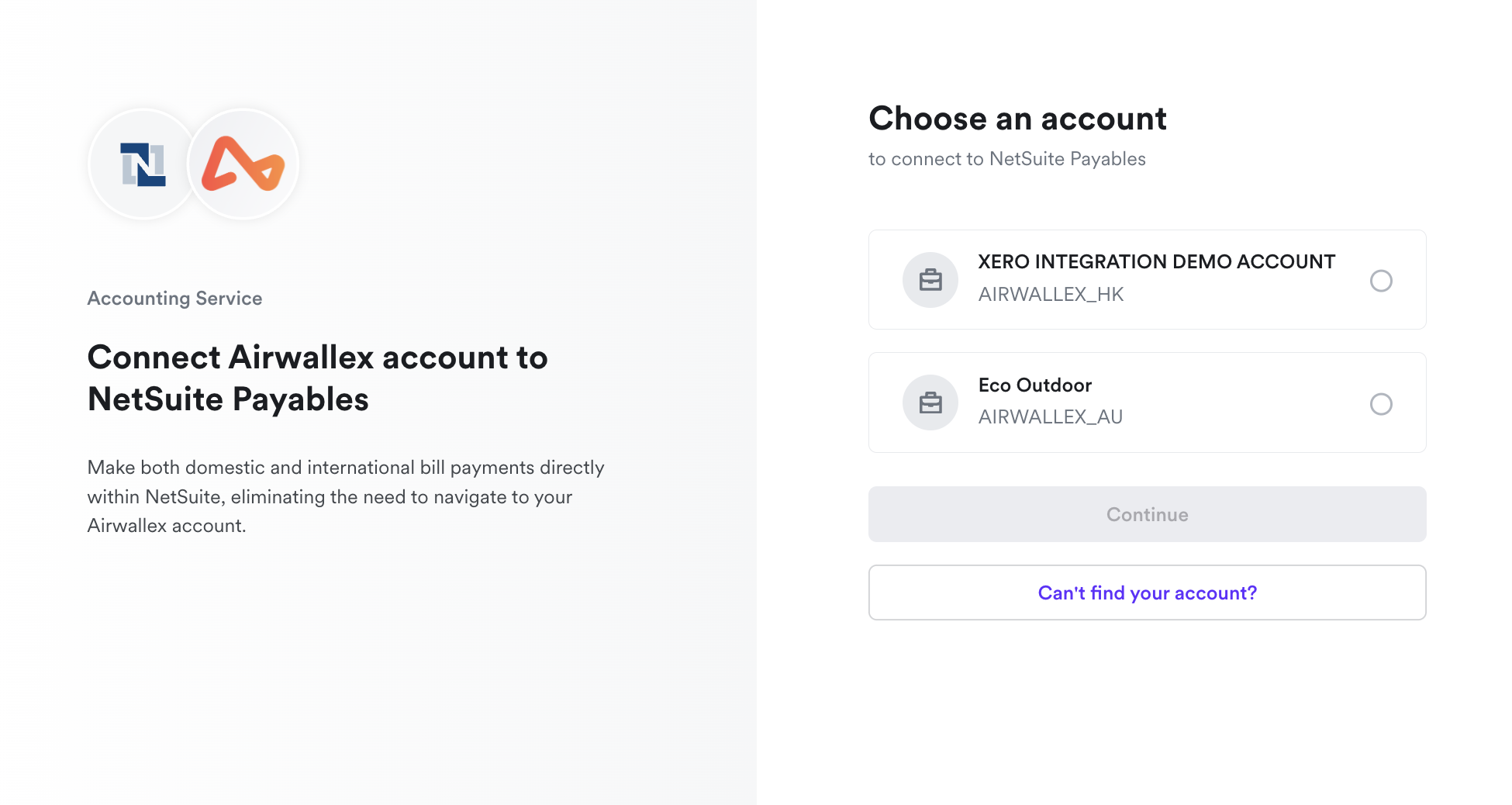
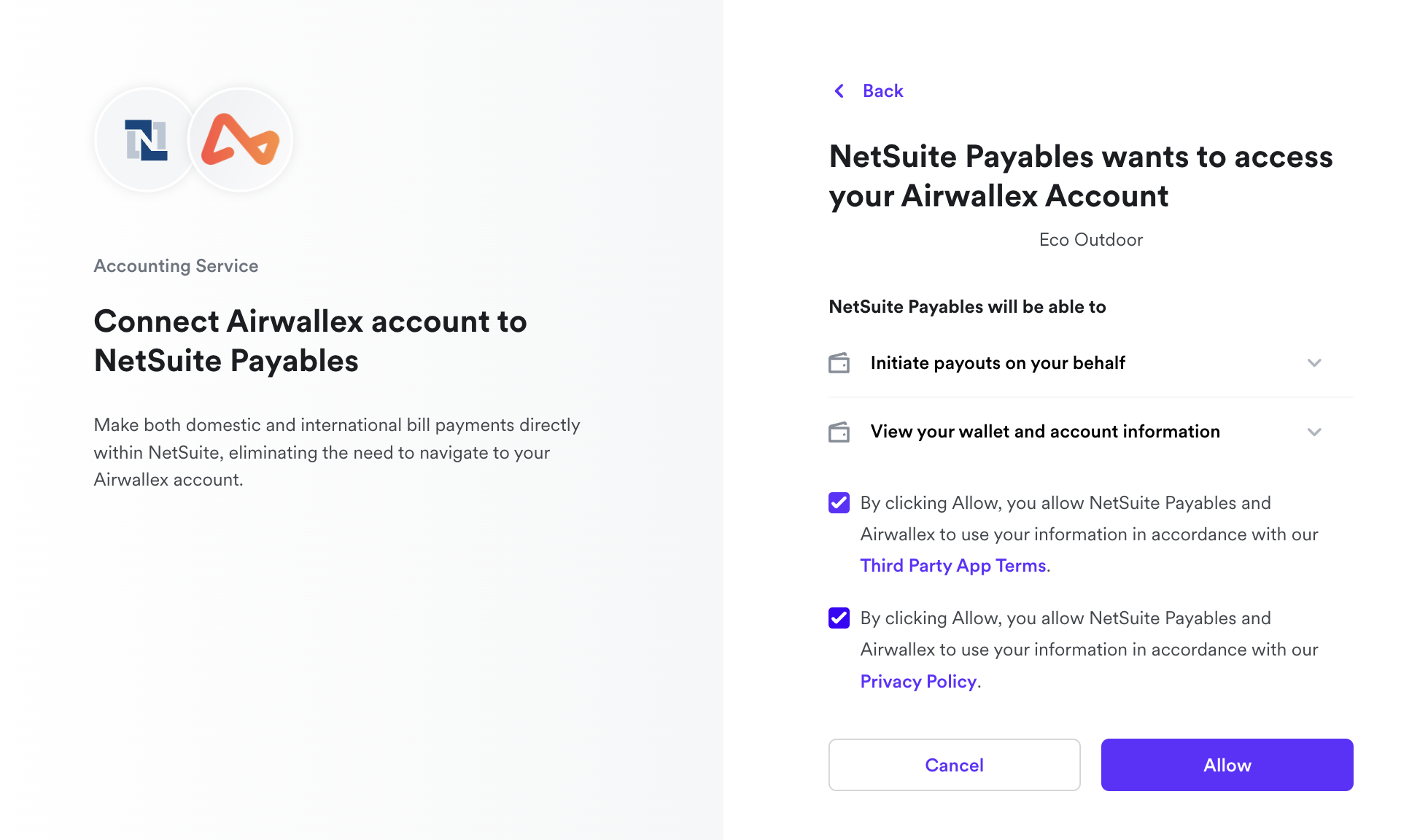
Upon granting consent for your application to access their Airwallex account, users will be redirected back to YOUR_REDIRECT_URI with an authorization code. In the event of non-consent, Airwallex will redirect users back to YOUR_REDIRECT_URI, accompanied by an error notification Otherwise, Airwallex will redirect back to YOUR_REDIRECT_URI with an error.
https://YOUR_REDIRECT_URI/?code=AUTH_CODE
Redirect URIs must be whitelisted for security purposes; if you intend to add a new redirect URI, contact your Airwallex partnerships manager to do so. Attempting to use a non-whitelisted redirect URI will result in an error.
Step 2: Obtain refresh and access tokens
After successfully acquiring the authorization code, your application should exchange the authorization code back to Airwallex OAuth server for a refresh and access token.
Shell1 curl --request POST \2 --url 'https://api.airwallex.com/oauth/token' \3 --header 'Content-Type: application/x-www-form-urlencoded' \4 --data-urlencode 'client_id=YOUR_CLIENTID' \5 --data-urlencode 'client_secret=YOUR_CLIENT_SECRET' \6 --data-urlencode 'code=AUTH_CODE' \7 --data-urlencode 'grant_type=authorization_code' \8 --data-urlencode 'redirect_uri=YOUR_REDIRECT_URI'
Note that YOUR_REDIRECT_URI must match the one that was used to obtain the AUTH_CODE in the previous step.
If the AUTH_CODE is valid, you will receive a refresh and access token. The refresh token is long-lived (valid for 90 days). You should store this securely in a database for refreshing your access token later. The access token is short-lived (valid for 5 minutes) and should be used in each session where you call the Airwallex API on behalf of authorized accounts.
JSON1 {2 "access_token": "eyJhbGciOiJIUzI1NiJ9.eyJzdWIiOiJ0b20iLCJyb2xlcyI6WyJ1c2VyIl0sImlhdCI6MTQ4ODQxNTI1NywiZXhwIjoxNDg4NDE1MjY3fQ.UHqau03y5kEk5lFbTp7J4a-U6LXsfxIVNEsux85hj-Q",3 "account_id": "acct_AcFEnD6CMgOvuFYLgFCw9A",4 "expires_in": 300,5 "refresh_token": "TIg7rEHqjxP3WOkGGS2S-J1GxQnZiAe8VCF7r6G5JMJSC_0l9qU7nyHVPjaQd298H",6 "refresh_token_expires_in": 7776000,7 "scope": "r:awx_action:balances_view r:awx_action:settings.account_details_view r:awx_action:global_accounts_view",8 "token_type": "bearer"9 }
To use the access token, pass the access token value in the Authorization header of requests each time your application calls an API. The value should always be: Authorization: Bearer {AccessToken}. For example, you can now call the GET /api/v1/account/ endpoint to obtain details about the account that was just connected.
Shell1 curl --request GET \2 --url 'https://api.airwallex.com/api/v1/account' \3 --header 'Authorization: Bearer <your_bearer_token>' \
Step 3: Refresh access tokens
As the access token is short-lived, you will need to obtain new access tokens to continue accessing the Airwallex APIs across sessions. To do so, use the latest refresh token value from your previous call to /oauth/token/.
Shell1 curl --request POST \2 --url 'https://api.airwallex.com/oauth/token' \3 --header 'Content-Type: application/x-www-form-urlencoded' \4 --data-urlencode 'client_id= YOUR_CLIENTID' \5 --data-urlencode 'client_secret=YOUR_CLIENT_SECRET' \6 --data-urlencode 'grant_type=refresh_token' \7 --data-urlencode 'refresh_token=REFRESH_TOKEN'
This will give you a new access token and refresh token. You should replace the previously-stored refresh token value with the new one. Note that the previous refresh token remains valid for 1 minute after the issuance of the new one. In case of any unexpected errors, such as a network outage, you can use the old refresh token to request new access and refresh tokens.
Do not attempt to use old refresh tokens to obtain a new access token. Doing so will cause the connection to be invalidated, as Airwallex interprets that as a potential signal that your refresh tokens were leaked or compromised by a third party.
JSON1 {2 "access_token": "eyJhbGciOiJIUzI1NiJ9.eyJzdWIiOiJ0b20iLCJyb2xlcyI6WyJ1c2VyIl0sImlhdCI6MTQ4ODQxNTI1NywiZXhwIjoxNDg4NDE1MjY3fQ.UHqau03y5kEk5lFbTp7J4a-U6LXsfxIVNEsux85h",3 "account_id": "acct_AcFEnD6CMgOvuFYLgFCw9A",4 "expires_in": 300,5 "refresh_token": "i-IPN3DIkTfNJ3dSVy0ea-QOtMAt0eVdx5OccrD-MNFJcFeHBnyUQZA60IlIi-EAH",6 "refresh_token_expires_in": 7776000,7 "scope": "r:awx_action:balances_view r:awx_action:settings.account_details_view r:awx_action:global_accounts_view",8 "token_type": "bearer"9 }
Access tokens may become invalid under the following circumstances:
- Expiration: If the access token expires, utilize your refresh token to renew it.
- User revocation: In the event that a user disconnects their Airwallex account from your application, both the access token and refresh token are invalidated. In such cases, it is necessary to prompt your users to initiate the authorization flow once again.
To prevent this, build a flow to get a new refresh_token every 90 days so the connection remains valid.