Strong Customer Authentication: A guide for merchants

Tilly Michell
Content Marketing Manager

For the past few years, electronic payment transactions between European businesses and customers have required an additional step, when certain conditions are met. Once card details are filled out, an e-wallet activated or contactless device tapped, buyers will be redirected to a page asking them to provide an additional layer of proof that they are not fraudsters. This step may involve filling out a password, for example, or receiving a text with a code that must be entered to complete the transaction.
This process is called Strong Customer Authentication (SCA), and it’s designed to make electronic payments safer. If an additional level of authentication is not completed, and if the transaction isn’t exempted from SCA rules, the buyer’s bank will decline the transaction. As customers, we may not think twice about filling in those extra details, but as merchants, it’s vitally important to get SCA right. A balance needs to be struck between staying compliant while also keeping the user experience as frictionless as possible.
In this article, we’ll explain everything merchants need to know about SCA, how to implement it correctly, and how requirements are likely to shift in the future.
What is Strong Customer Authentication?
Strong Customer Authentication (SCA) is a European regulatory requirement that aims to make electronic transactions more secure. It became applicable in 2019, when the European Union's Revised Payment Services Directive (PSD2) took effect. It applies to electronic transactions within the European Economic Area (EEA).
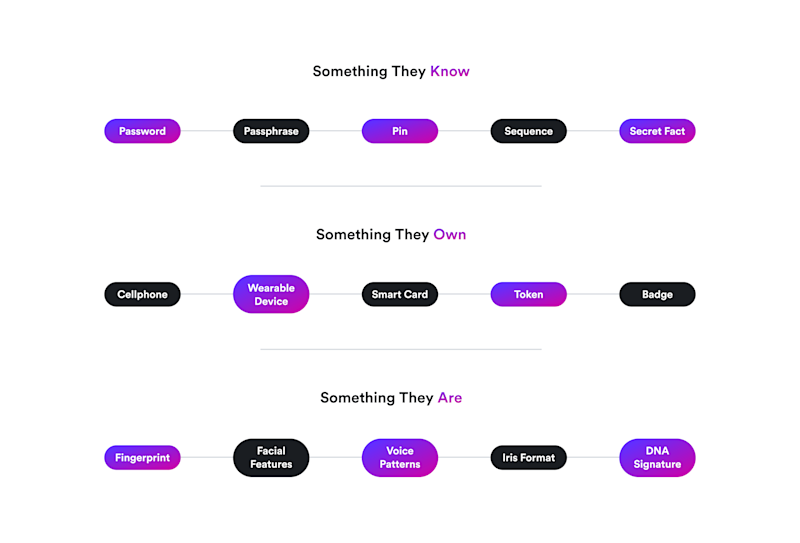
When a customer makes an online or contactless transaction in Europe, they must prove the payment is legitimate by providing at least two out of the three possible elements:
Something they know – e.g. password or PIN
Something they have – e.g. phone or smart card
Something they are – e.g. fingerprint or facial scan
For example, a transaction is compliant with SCA standards if a customer is required to scan their fingerprint using their phone, and is then texted a code to their phone which they have to enter correctly to complete the transaction.
This is a more secure process than simply asking customers to fill out a password. Customers often use the same password for multiple purposes, so a data breach at one company could compromise this form of authentication. There are other ways that fraudsters can gain passwords, for example through: phishing (spoofing a company and asking for information), brute-force attacks (trying all possible character combinations) and man-in-the-middle attacks (intercepting information as it is passed to a legitimate destination.) Requiring multiple forms of authentication makes it much harder for fraudsters to succeed in completing illegitimate transactions.
Unlock global growth
Is SCA required in the UK?
Yes, businesses that operate in the UK and Monaco must meet SCA requirements, as well as businesses that operate in the EEA. When the UK left the EU on 31 Jan 2020 it was in the process of implementing SCA requirements, and these came into force in March 2022.
Understanding PSD2
The original Payment Services Directive came into force in 2009. It aimed to establish a legal framework for payment services within the EEA, and to promote competition, innovation, and consumer protection in payment services.
This piece of legislation was subsequently updated to keep pace with the evolution of payment technology and the evolving threat of fraud. The second version of the Payment Services Directive, known as PSD2, took effect in 2018. It introduced additional measures, including the requirement for Strong Customer Authentication (SCA) to enhance the security of electronic transactions.
Another key feature of PSD2 is known as Access to Account (XS2A). PSD2 allows third-party providers (TPPs) to access account information held by banks with the customer's consent to provide additional financial services.
TPPs are divided into two categories in PSD2. Account Information Service Providers (AISPs) can access and retrieve account information; an example could be a service offering personalised financial advice. Payment Initiation Service Providers (PISPs) can initiate payment transactions on behalf of users, such as a mobile payment app.
SCA requirements and exemptions
As outlined above, SCA under PSD2 requires the use of two or more different categories of authentication during electronic transactions. However, there are exemptions to this rule for transactions considered low-risk or low-impact. SCA may not be required when the following specifications are present:
The transaction is low-value.
A “trusted beneficiary” is the recipient of the transaction. Customers can add merchants to a trusted whitelist, which means SCA is generally only required on the initial transaction.
Secure corporate payment processes are used to initiate the transaction, using an eligible card.
Transaction Risk Analysis (TRA) has been used to assess a transaction as low-risk.
In addition to these exemptions, SCA doesn’t apply to transactions that are out of the scope of the regulations. These include transactions where either the issuer or acquirer is outside of the EEA, a gift card (or another anonymous payment method) is used, an order is placed by phone or mail, or when a cardholder has pre-agreed and pre-authenticated a transaction.
Impact of SCA on businesses and consumers
Although SCA requires extra work for businesses and extra steps for customers to complete a transaction, it is designed to be in the interests of both groups. Consumers gain a greater degree of protection from fraud, and businesses benefit from a greater level of trust in online transactions, and more innovation in the fintech space.
Businesses need to balance multiple requirements when designing their checkout flow in compliance with SCA. They need to ensure the process remains smooth enough that customers don’t abandon their carts without completing the transaction. At the same time, merchants need to introduce the necessary forms of authentication, monitor which types of transaction are exempt and make sure these go through without unnecessary additional steps.
Implementing Strong Customer Authentication
SCA methods and technologies
Merchants don’t necessarily need a detailed technological understanding of every process that goes into SCA. However, it can be helpful to have a grasp of key concepts and pieces of terminology. These include:
Two-factor authentication (2FA): This is the central requirement of SCA. There are three essential types (or ‘factors’) of authentication, as laid out by PSD2. The knowledge factor (passwords, PINs, personal facts such as the name of first pet), the possession factor (mobile devices, smart phones, tokens) and what’s called the inherence factor (data based on who you are, such as your fingerprint, facial features, iris or voice.) 2FA is the requirement that two of these three factors are used for authentication.
Multi-factor authentication (MFA): Essentially, this means the same thing: more than one authentication factor should be used. Technically, it’s a broader category, as it encompasses two or more authentication factors.
Biometric authentication: The use of unique biological traits to confirm a person’s identity. The “inherence” factor relies on biometric data in order to authenticate transactions.
Digital payment apps like Apple Pay often use biometric methods such as a fingerprint scan to quickly and seamlessly authenticate payments. As these payments are completed on the customer’s digital device, this fulfils the two-factor authentication requirement, as possession of the phone or device itself counts as one factor.
The role of payment processors
Payment processors play a crucial role in enabling Strong Customer Authentication (SCA), commonly by using protocols like 3D Secure (3DS). This involves integrating with card networks and issuers to enable the secure authentication process.
When a customer initiates an online transaction, the payment processor, through 3DS, may redirect the user to an authentication page hosted by the card issuer. This page prompts the user to authenticate their identity.
Payment processors can incorporate dynamic risk assessment mechanisms to ensure that additional authentication is not requested when it is not necessary. Low-risk transactions may be exempt from certain authentication steps.
3D Secure authentication with Airwallex
Airwallex offers payment processing with 3D Secure protocols for card payments. Our 3DS engine automatically picks the best strategy based on transaction risk, applicable regulatory exemptions, and policies. This process enables merchants to maximise global payment acceptance rates whilst staying compliant with PSD2 regulations in applicable jurisdictions.
The future of Strong Customer Authentication
PSD3 and PSR
A third version of the European Payment Services Directive (PSD3) is currently in the works. A draft proposal was published in June 2023, alongside plans for a new Payments Services Regulation (PSR). Together, these requirements aim to enhance innovation in payments technology while improving customer rights and trust in financial data sharing.
These pieces of legislation are expected to take effect in around 2026 or 2027. When this happens, the SCA standards that businesses must implement when accepting payments are likely to be upgraded. The proposal also suggests that SCA will be changed to make it more accessible to disabled persons and others who may have difficulty using the current authentication methods.
Other likely changes to legislation include:
Extending refund rights to people who made authenticated payments because they fell victim to fraud. For example, those who were tricked into sending money to someone pretending to be a bank, company, fine or online romantic partner.
Making it mandatory to check that recipient’s IBANs align with their account names for all credit transfers.
Enabling access to financial data, with customers’ consent, for non-bank payment service providers, so they can offer innovative financial products.
Evolution of authentication technologies
The last decade has seen rapid change in the development of authentication technologies. It was 2013 when Apple introduced Touch ID with the iPhone 5s, making fingerprint recognition mainstream on smartphones. In 2017, the iPhone X featured Face ID for the first time.
Since then, in-display fingerprint sensors have been developed, so a fingerprint can be scanned by touching a screen rather than a specific sensor. Laptops and tablets have also begun to incorporate biometric scanning technology.
This evolution is continuing at high speed:
There has been progress in 3D facial recognition, which enhances security by creating detailed depth maps of the user's face. As technology advances, biometrics are likely to play an even more integral role in securing digital identities across devices and applications.
Ongoing research is happening in the arena of behavioural biometrics, such as gait recognition and typing pattern analysis. These methods can provide continuous authentication based on user behaviour.
Contextual authentication is another buzzword. This concept involves verifying a person’s identity based on contextual factors, such as device recognition, location, and user behaviour. It is gaining importance as a method of enhancing security while minimising friction.
Integration with emerging technologies
Blockchain technology may play a role in the future in enhancing the security and transparency of financial transactions. It could be integrated into authentication processes for decentralised and tamper-resistant verification.
Advanced AI algorithms and machine learning models are also increasingly being employed to analyse user behaviour, detect anomalies, and improve the accuracy of risk assessments. This can potentially contribute to more adaptive and intelligent authentication systems.
Take control of your risk strategy with Airwallex
Airwallex is a global payments and financial platform that helps businesses maximise acceptance rates whilst staying compliant with regulations, no matter where in the world they operate. Businesses of all shapes and sizes use Airwallex to reach new international customers and eliminate unnecessary currency conversion fees. Payments can be accepted in 180+ countries via 160+ local payment methods. Click here to find out more about Airwallex Payments.
Streamline your financial operations

Tilly Michell
Content Marketing Manager
Tilly manages the content strategy for Airwallex. She specialises in content that supports businesses in their growth trajectory.
Posted in:
Online payments

